“工会杯”2025年自治区工业和信息化技能竞赛WP,题目附件文件请看最下方百度网盘下载,可以下载该比赛的所有题目和镜像
调度中心未解密的邮件
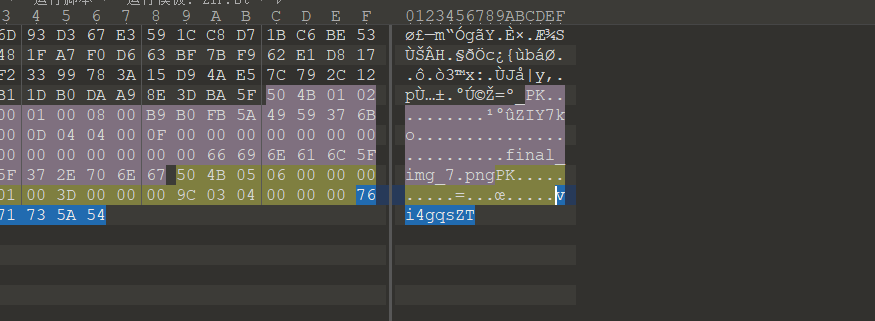
010打开最后发现密码

vi4gqsZT
解压拿到照片

PNG修改宽高

达梦数据库日志分析
解压打开flag明文

文档里的陷阱
直接010打开flag在最后

轻量级分组密码
ai脚本
from hashlib import md5
def bytes_to_long(b):
return int.from_bytes(b, byteorder=”big”)
def long_to_bytes(n, length=None):
if length is None:
length = (n.bit_length() + 7) // 8
return n.to_bytes(length, byteorder=”big”)
class ElectricityCipher:
S_BOX = [
0x3, 0xB, 0x5, 0xE, 0x6, 0xC, 0x4, 0xF,
0x7, 0xD, 0x1, 0x0, 0xA, 0x2, 0x8, 0x9
]
INV_S_BOX = [0] * 16
for i, v in enumerate(S_BOX):
INV_S_BOX[v] = i
ROUNDS_CONFIG = {
64: 16,
80: 18,
128: 20
}
def __init__(self, key: int, key_size: int = 64):
if key_size not in self.ROUNDS_CONFIG:
raise ValueError(“无效的密钥长度,必须是64/80/128位”)
self.key = key
self.key_size = key_size
self.rounds = self.ROUNDS_CONFIG[key_size]
self.round_keys = self._key_expansion(key, key_size)
@staticmethod
def _nibble_sub(state, s_box):
return [s_box[nibble] for nibble in state]
@staticmethod
def _shift_rows(state, inverse=False):
matrix = [state[i:i+4] for i in range(0, 16, 4)]
for i in range(4):
if inverse:
matrix[i] = matrix[i][-i:] + matrix[i][:-i]
else:
matrix[i] = matrix[i][i:] + matrix[i][:i]
return [n for row in matrix for n in row]
@staticmethod
def _linear_transform(n):
return ((n & 1) << 3) | (n >> 1)
@staticmethod
def _inv_linear_transform(n):
return ((n << 1) & 0xF) | (n >> 3)
def _mix_columns(self, state):
columns = [[state[i], state[i+4], state[i+8], state[i+12]] for i in range(4)]
for _ in range(4):
new_cols = []
for col in columns:
v0, v1, v2, v3 = col
w0 = v1
w1 = v2 ^ self._linear_transform(v3)
w2 = v3
w3 = self._linear_transform(v0) ^ v1
new_cols.append([w0, w1, w2, w3])
columns = new_cols
return [col[i] for i in range(4) for col in columns]
def _inv_mix_columns(self, state):
for _ in range(4):
cols = [state[i::4] for i in range(4)]
new_cols = []
for col in cols:
w0, w1, w2, w3 = col
v1 = w0
v3 = w2
v0 = self._inv_linear_transform(w3 ^ v1)
v2 = w1 ^ self._linear_transform(v3)
new_cols.append([v0, v1, v2, v3])
state = [new_cols[i][j] for j in range(4) for i in range(4)]
return state
def _add_round_key(self, state, round_key):
return [s ^ k for s, k in zip(state, round_key)]
def _key_expansion(self, key: int, key_size: int):
if key_size == 64:
w, lam = 16, 4
elif key_size == 80:
w, lam = 20, 5
else:
w, lam = 32, 8
total_bits = w * 4
nibbles = []
for i in range(total_bits-4, -4, -4):
nibbles.append((key >> i) & 0xF)
reg = nibbles[:]
lfsr = 0b11111
round_keys = []
for r in range(self.rounds + 1):
round_key = reg[:16]
round_keys.append(round_key)
if r < self.rounds:
feedback = ((lfsr >> 4) ^ (lfsr >> 2)) & 1
lfsr = ((lfsr << 1) | feedback) & 0b11111
for i in range(5):
bit_pos = total_bits – 1 – i
nibble_idx = bit_pos // 4
bit_in_nibble = 3 – (bit_pos % 4)
current = reg[nibble_idx]
lfsr_bit = (lfsr >> (4 – i)) & 1
new_bit = ((current >> bit_in_nibble) & 1) ^ lfsr_bit
reg[nibble_idx] = (current & ~(1 << bit_in_nibble)) | (new_bit << bit_in_nibble)
matrix = [reg[i*lam:(i+1)*lam] for i in range(4)]
matrix[0] = [self.S_BOX[n] for n in matrix[0]]
reg = [n for row in matrix for n in row]
matrix = [reg[i*lam:(i+1)*lam] for i in range(4)]
for i in range(4):
shift = i + (3 if key_size == 80 else 0)
matrix[i] = matrix[i][shift % lam:] + matrix[i][:shift % lam]
reg = [n for row in matrix for n in row]
columns = [reg[i::4] for i in range(4)]
for _ in range(4):
new_cols = []
for col in columns:
v0, v1, v2, v3 = col
w0 = v1
w1 = v2 ^ self._linear_transform(v3)
w2 = v3
w3 = self._linear_transform(v0) ^ v1
new_cols.append([w0, w1, w2, w3])
columns = new_cols
matrix = [[col[i] for col in columns] for i in range(4)]
reg = [n for row in matrix for n in row]
return round_keys
def decrypt(self, ciphertext: int) -> int:
state = [(ciphertext >> (60 – i*4)) & 0xF for i in range(16)]
for r in range(self.rounds, 0, -1):
state = self._add_round_key(state, self.round_keys[r])
if r < self.rounds:
state = self._inv_mix_columns(state)
state = self._shift_rows(state, inverse=True)
state = self._nibble_sub(state, self.INV_S_BOX)
state = self._add_round_key(state, self.round_keys[0])
plaintext = 0
for i, nibble in enumerate(state):
plaintext |= nibble << (60 – i * 4)
return plaintext
if __name__ == “__main__”:
key = 0x0123456789ABCDEF
ciphertext = b’)6\x10\xd0\xd9\x87\x8c\x83′
ct_int = bytes_to_long(ciphertext)
cipher = ElectricityCipher(key, 64)
pt_int = cipher.decrypt(ct_int)
magic = long_to_bytes(pt_int, 8) # 64位 = 8字节
print(“[*] magic =”, magic)
print(“[*] flag =”, b”flag{” + md5(magic).hexdigest().encode() + b”}”)
寻找SMTP协议
放入软件
flag1

flag2

flag3

flag part3: YzBsX0FuQGx5c2lzXzIwMjU=
flag part2: 9TTVRQX1Byb3Rv
flag part1: V2VsYzBtZV90MF
拼接解密

flag{}包裹
暂无评论内容